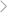Benefits from Keylogger Features
Logs All Kids Type on Keyboard
Get the Password of the Software
Keywords Tracking & Alerts

Logs All Kids Type on Keyboard
See all the keystrokes that occur on the monitored devices. Each keystroke has a name and an app icon that identifies its origin.
- Clear vision of detailed messages and chatting content from Messages and social apps.
- Get to know what interests your kids on the Internet and what they surf on the search engine.
- Everything children note down on memos or calendars will be tracked, too.
Available for:
Get the Password of Software Easily
Catch every keyword activity, even the passwords typed.
- Though in security mode when entering keywords, FamiGuard Pro can record these keystrokes.
- Have control of kids' accounts for better and comprehensive parental control.
Available for:

Keywords Tracking & Alerts
You will be notified with emails or dashboard notifications if specific keywords or phrases appear.
- Set up a single keyword or a whole phrase to set alerts.
- In the dashboard, you can see keywords, where they are detected, actual messages related to them, and when they appear.
- If keywords happen on some apps like WhatsApp and Telegram, this keylogger will take screenshots, and you can check screenshots for details.
Available for:
Explore Parental Control Tools to Safeguard Your Child
Set up FamiGuard Pro in 3 Simple Steps
1. Sign up Free and Choose Your Plan
Register for a free FamiGuard account and choose a suitable subscription plan.
Buy Now
2. Follow the Setup Guide
Download, installation, and configuration. Whether manually or , that is easy.
3. Operate on Dashboard Panel and Begin Tracking
Anytime you want to monitor keystrokes, you can check details from Phone Files > Keylogger. And if you're going to track keywords or set content alerts, access Remote Control > Track Keywords.
View Demo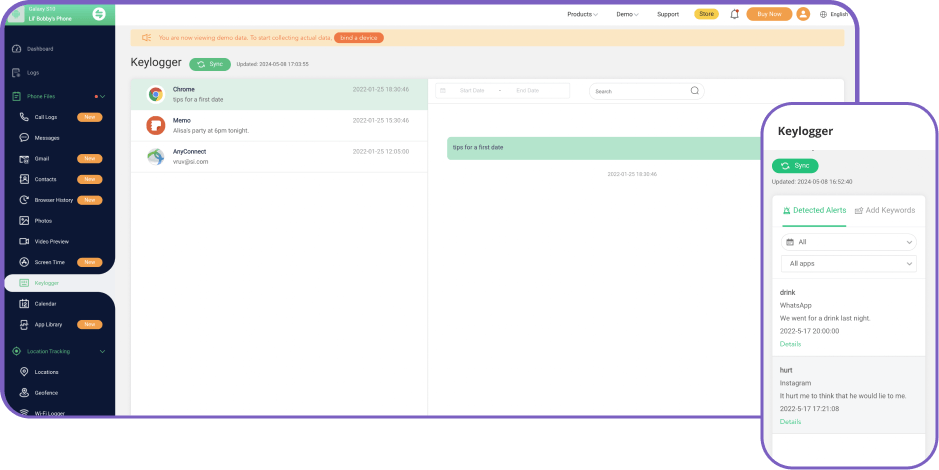
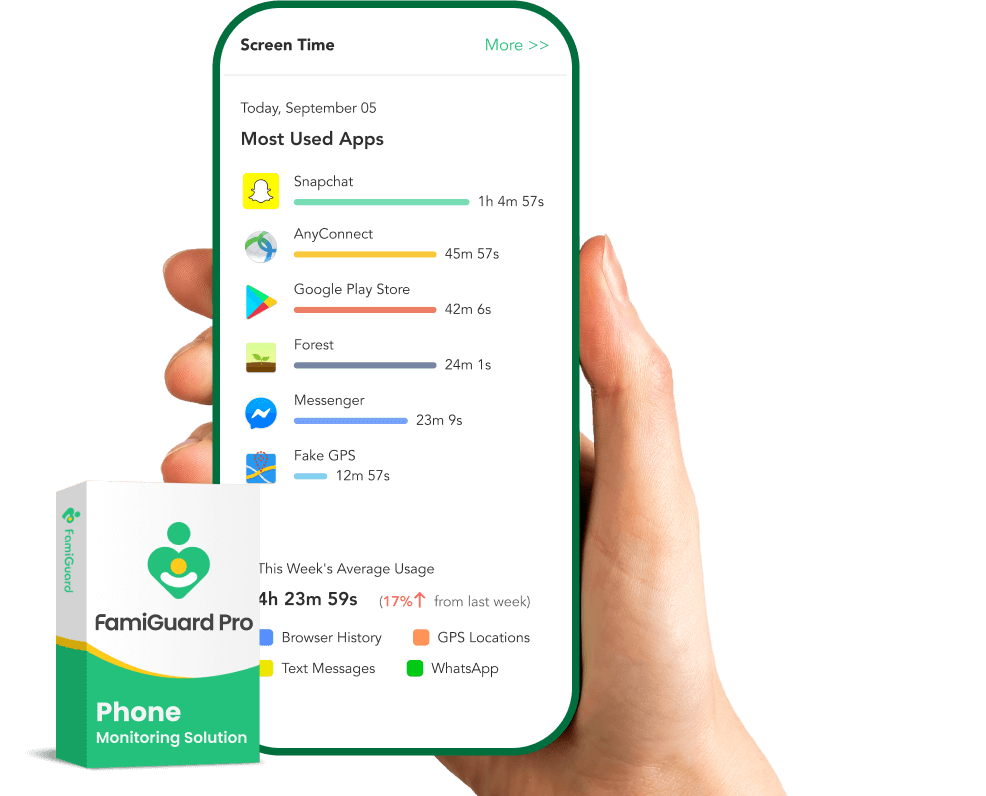
Best Phone Tracker for Parental Control
Start your phone monitoring with FamiGuard Pro today and keep your child safe online.
FAQs About Phone Keylogger:
-
1. Is there a built-in keylogger?
Yes. Some operating systems and software may have built-in keylogging functionality for legitimate purposes such as system diagnostics, accessibility features, or user experience improvement.
-
2. Is it safe to download a keylogger?
Downloading and using a keylogger without proper authorization and legal consent is unethical and may be illegal. Additionally, keyloggers can pose significant security risks as they can capture sensitive information such as passwords, credit card numbers, and personal messages.
-
3. Does VPN prevent keylogging?
No. A Virtual Private Network (VPN) encrypts internet traffic between the user's device and the VPN server, which can help protect against eavesdropping and man-in-the-middle attacks. However, VPNs do not directly prevent keylogging on the user's device. Users should employ additional security measures such as using reputable antivirus software and being cautious about downloading and installing unknown software.
-
4. Does Windows 10 have a built-in keylogger?
Windows 10 has features that may collect telemetry data for system diagnostics and user experience improvement, but it does not have a built-in keylogger for malicious purposes. Users can control privacy settings in Windows 10 to limit data collection and telemetry reporting.
-
5. Is keylogging a felony?
The legality of keylogging depends on factors such as the jurisdiction, purpose, and consent of the parties involved. In many cases, unauthorized keylogging or using keyloggers for malicious purposes may be illegal and result in criminal charges such as identity theft, fraud, or invasion of privacy.
Related Topics about Keylogger
7 Best Keylogger for Windows 10/11 That You Should Try
This guide will introduce you to the top seven keyloggers for Windows and help you decide which one is best for you. We will cover the features, pros, and cons of each keylogger to give you a comprehensive understanding of your options. So, let's dive in!
8 Best Keylogger Apps for iPhone
In this guide, we'll explore some of the best keylogger apps for iPhone users. We'll discuss the features, pros, and cons of each app to help you choose the right one for your needs. So if you're ready to get started, here we go!