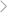FamiGuard Support: Monitor Devices with Others' Permission.
Is It Possible to Hack a Phone?
Absolutely! However, monitoring is not as intricate as it may seem, provided you possess the appropriate knowledge. It is worth noting that monitoring an Android smartphone is comparatively simpler than monitoring an iPhone.
Within this article, we will demonstrate 5 methods that can be employed to easily to solve the problem of how to monitor into someone's phone. Additionally, we will outline steps you can take to enhance the security of your phone and protect it from potential hackers. Stay engaged to find out more!"
Table of Contents
Part 1: How to Hack Someone's Phone – 5 Effective Ways
People exploit the internet as a means to deceive and defraud others, leading to financial losses. Among these activities, monitoring has emerged as the most effective solution. Therefore, to know more s in other people's phone, 5 effective methods detailing how to monitor into someone's cell phone would be showed in the following part!
Way 1: Hack Phones with Keylogging App
To find the answer of how to monitor into someones phone, Keylogger is a good choice, which can capture and record all keystrokes and device activity in within a period of time, making them a particularly intriguing method for monitoring mobile phone activities. By utilizing a keylogger, you can effectively capture and record all keystrokes made on the target device.

If you are interested keylogger apps, you can try FamiGuard Pro, which does a great job of recording other people's phone passwords for you. The recording process is completely invisible, so you don't have to be afraid of being caught.
Way 2: Hack Phones with Phishing link
"Could my phone be hacked with phishing link?" Definitely yes! it is possible for your phone to be hacked through a phishing link. Phishing is a technique used by hackers to trick individuals into revealing sensitive information or gaining unauthorized access to their devices or accounts. Phishing links are designed to appear legitimate, often imitating well-known websites or services, and when clicked, they can lead you to fake login pages or malicious websites that may exploit vulnerabilities in your phone's software.

To protect yourself from falling victim to phishing attacks, it's important to exercise caution while clicking on links, especially if they are received from unknown or suspicious sources. Here are a few tips to help prevent phishing attacks:
Be vigilant: Be skeptical of unexpected emails, text messages, or social media messages that ask you to click on links or provide personal information.
Verify the source: Double-check the sender's email address or the website URL to ensure they are legitimate. Look for any signs of misspellings or variations that may indicate a fraudulent source.
Way 3: Hack Phones with Man-in-the-Middle Wi-Fi Attack
A Man-in-the-Middle (MitM) Wi-Fi attack occurs when a malicious actor intercepts communication between a user's device and a Wi-Fi network. In this attack, the attacker positions themselves between the user's device and the intended network, allowing them to intercept and potentially manipulate the data being transmitted.

Here's a simplified explanation of how a MitM Wi-Fi attack works:
- The attacker sets up a rogue Wi-Fi access point that mimics a legitimate network (e.g., a public Wi-Fi hotspot).
- Unsuspecting users connect to the rogue access point, thinking it is a legitimate network.
- All data transmitted between the user's device and the rogue access point passes through the attacker, who can intercept, view, or modify the data.
- The attacker may perform actions such as capturing login credentials, injecting malicious code or content into websites, or eavesdropping on sensitive information.
Regarding the security of your phone, it is possible for your device to be compromised through a MitM Wi-Fi attack if you connect to a malicious or compromised Wi-Fi network.
Way 4: Hack Phones with Bluetooth
Skilled monitors have the capability to employ specialized technologies that scan for susceptible mobile devices having an active Bluetooth connection. These attacks can be executed when the monitors are within proximity of your phone, typically within a 30-foot range, particularly in crowded locations.

When the monitors establish a Bluetooth connection with your phone, there is a potential for them to gain access to your data and information. However, it's important to note that the retrieval of such data and information can only occur while the phone remains within the cybercriminal's range. As you may have inferred, this type of attack is considered more sophisticated due to the effort and advanced technology involved.
Way 5: Hack Phones with SIM card Swapping
Every Android and iPhone device is equipped with a SIM (subscriber identity module) card. A method of gaining access to someone's phone involves swapping the SIM card. Hackers may approach a mobile carrier such as Verizon, T-Mobile, or another provider to obtain a new SIM card, thereby deactivating the old one.
With the new SIM card in hand, it becomes relatively simple to take control of the targeted person's phone. By swapping the SIM card, you gain the ability to access their phone calls, text messages, and other information.
Part 2: How to Hack Someone's Phone Remotely?
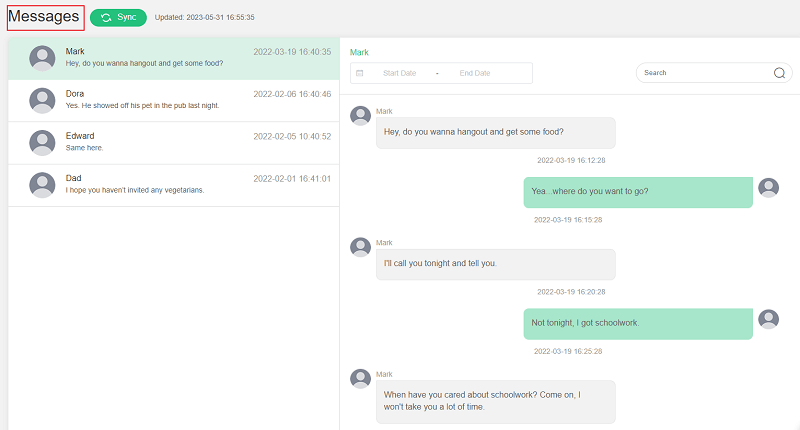
Now that you've learned the 5 effective ways to monitor someone's Phone, here, we would like to introduce you the most effective way to monitor other people's Phone. With this tool, you can easily access to someone else's phone and monitor all activities happened on that, such as videos, pictures and files.
FamiGuard Pro
Rate:
Of all these Phone-monitoring apps, FamiGuard Pro is the best. All you need is physical access to the target phone and install this app, then you can easily monitor into someone's Phone and see all his or her content!

Amazing Features of FamiGuard Pro for Android
-
Remote Control: You can view his or her phone videos and pictures , without touching the target phone.
-
Keylogger Feature: It has a keylogger feature that records everything typed on the keyboard.
-
Stealth Mode: No app icon appears on the target phone and the monitored person will not detect that you are monitoringing on his phone.
-
Monitoring Social Media Apps: Viewing messages or pictures on WhatsApp, Tiktok, Facebook, Viber, Tinder, Telegram, Instagram, Snapchat, WeChat, and more
If you want to monitor into iPhone or iPad, you can try FamiGuard Pro for iOS
FAQs: Hot Questions about How to Hack Phone
1. Can someone monitor my phone without the access to my phone?
It is highly unlikely for someone to monitor your phone without having physical or access to it. Hacking typically requires some form of interaction with the targeted device, whether it's physical access to install phone-monitoring apps or exploiting vulnerabilities through means such as phishing attacks or malware.
2. How do monitors get your phone password?
Hackers can employ various methods to obtain your phone password. Here are a few common techniques like brute-Force attacks, social engineering and data breaches.
By Tata Davis
An excellent content writer who is professional in software and app technology and skilled in blogging on internet for more than 5 years.