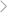FamiGuard Support: Monitor Devices with Others' Permission.
If you're interested in how to monitor someone's iMessage, you've come to the right resource. This article will provide you with the necessary guidance on how to monitor into someone's iMessage without any cost. You'll gain valuable knowledge about monitoring an iPhone and the essential tools required to accomplish this task effectively.
Table of Contents
Part 1: Why to Hack Someone's iMessage?
There can be various reasons why someone might want to monitor someone's iMessage. Here are a couple of common motivations:
Protecting your child: Parents may want to monitor their child's iMessages to ensure their safety and well-being. By monitoring into their iMessage, parents can keep an eye on their conversations, identify any potential risks or inappropriate content, and take appropriate actions to protect their child.
Checking partner's loyalty: In some cases, individuals may have suspicions about their partner's fidelity or trustworthiness. By monitoring into their partner's iMessage, they hope to gather evidence or confirm their doubts. However, it's important to note that invading someone's privacy without their consent can have legal and ethical implications.
Part 2: How to Hack Someones Imessage with Monitor Apps [Top 4]
1. FamiGuard Pro
If you want to ask "how to monitor iMessage?", then FamiGuard Pro for iOS is your best choice. It will help you scan the phone data. In this way, you could easily read someone's iMessage.
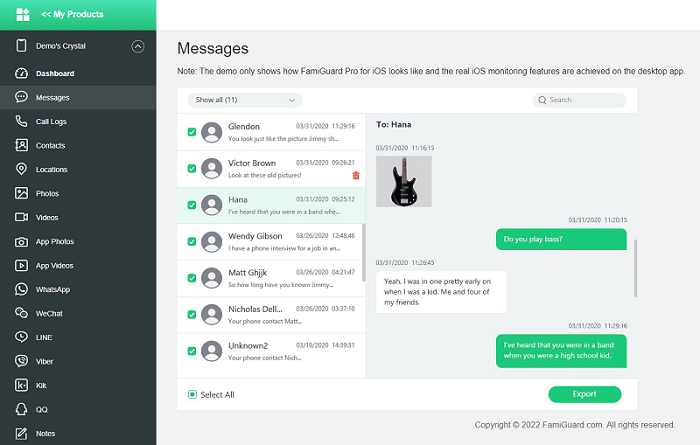
To monitor Someones Imessage using FamiGuard Pro for iOS, follow these steps:
Step 1: Sign up for a FamiGuard Pro account with a valid email.
Step 2: Purchase a plan and download the app onto your computer, following the setup guide.
Step 3: Use the on-screen instructions to access the target's iPad data.
2. CocoMonitor
This app is highly effective for monitoring both Android and iOS mobile devices discreetly. It offers excellent surveillance capabilities without raising any suspicion. The app is compatible with devices running iOS 7 and later versions, and one of its notable advantages is that it doesn't require installation on the target phone. All you need is the target's iCloud password, and you're ready to proceed with the monitoring process.

-
The app offers comprehensive tracking capabilities for various data types.
-
It enables monitoring of the target iPhone, allowing you to access and read iMessages without physical access to the phone.
Pros
-
The app does not provide the ability to intercept or block specific functions on the target phone, such as restricting access to certain websites.
-
It comes at a higher cost compared to some other monitoring solutions.
Cons
3. mSpy
This app is designed to monitor iMessages, providing valuable insights into the conversations your children, spouses, or employees are engaging in. It serves as a protective measure for parents, allowing them to safeguard their kids from potential dangers and enabling monitoring of employees and spouses through their messaging activities.
-
Supports keyword tracking for monitoring typed content.
-
Monitors popular social media platforms like LINE, KiK, and WhatsApp.
Pros
-
Requires jailbreaking of the phone for usage.
-
Limited number of social media sites supported for monitoring.
Cons
4. Spyic
Spyic is a powerful monitor app designed to monitor iMessages on your children's phones, ensuring their safety online. With compatibility for both iOS and Android devices, it offers comprehensive monitoring capabilities. In addition to iMessages, Spyic tracks SMS, social media messages, call history (including dates and numbers), providing valuable insights into your child's communication activities.
-
Monitoring an iPhone requires jailbreaking.
-
It offers an affordable solution for effective monitoring.
Pros
-
Requires jailbreaking of the phone for usage.
-
Rooting the target phone is necessary for optimal functionality, and without it, retrieving information may take up to 24 hours.
Cons
By Tata Davis
An excellent content writer who is professional in software and app technology and skilled in blogging on internet for more than 5 years.